Syntax hacking: Researchers discover sentence structure can bypass AI safety rules
New research offers clues about why some prompt injection attacks may succeed. Researchers from MIT, Northeastern University, and Meta recently released a paper suggesting tha
Published: 2025-12-02T12:15:55
Half of exposed React servers remain unpatched amid active exploitation
Wiz says React2Shell attacks accelerating, ranging from cryptominers to state-linked crews Half of the internet-facing systems vulnerable to a fast-moving React remote code execution flaw remain unpatched, even as exploitation has exploded into more
Published: 2025-12-12T11:31:09
Researchers spot 700 percent increase in hypervisor ransomware attacks
Get your Hyper-V and VMware ESXi setups in order, people Researchers at security software vendor Huntress say they ve noticed a huge increase in ransomware attacks on hypervisors and urged users to ensure they re as secure as can be and properly back
Published: 2025-12-09T06:41:27
Novel clickjacking attack relies on CSS and SVG
Who needs JavaScript? Security researcher Lyra Rebane has devised a novel clickjacking attack that relies on Scalable Vector Graphics (SVG) and Cascading Style Sheets (CSS).
Published: 2025-12-05T21:55:13
Pentagon's Signalgate report finds Pete Hegseth violated military policies
It has been months since a group of Trump administration officials put together a Signal group chat to discuss classified military intelligence ahead of a military strike in Yemen while inadvertently adding a journalist, and now the Pentagon's inspector general has released its report on the mess. The results of Steven Stebbins' eight-month-long investigation found […]  It has been months since a group of Trump administration officials put together a Signal group chat to discuss classified military intelligence ahead of a military strike in Yemen while inadvertently adding a journalist, and now the Pentagon's insp...
It has been months since a group of Trump administration officials put together a Signal group chat to discuss classified military intelligence ahead of a military strike in Yemen while inadvertently adding a journalist, and now the Pentagon's insp...
Published: 2025-12-04T16:55:09
CyberVolk’s ransomware debut stumbles on cryptography weakness
The pro-Russia hacktivist group CyberVolk launched a ransomware-as-a-service (RaaS) called VolkLocker that suffered from serious implementation flaws, allowing victims to potentially decrypt files for free. [...]
Published: 2025-12-13T10:11:21
Apple fixes two zero-day flaws exploited in 'sophisticated' attacks
Apple has released emergency updates to patch two zero-day vulnerabilities that were exploited in an "extremely sophisticated attack" targeting specific individuals. [...]
Published: 2025-12-12T18:23:25
Coupang data breach traced to ex-employee who retained system access
A data breach at Coupang that exposed the information of 33.7 million customers has been tied to a former employee who retained access to internal systems after leaving the company. [...]
Published: 2025-12-12T13:28:30
Fake ‘One Battle After Another’ torrent hides malware in subtitles
A fake torrent for Leonardo DiCaprio's 'One Battle After Another' hides malicious PowerShell malware loaders inside subtitle files that ultimately infect devices with the Agent Tesla RAT malware. [...]
Published: 2025-12-12T12:12:47
Shadow spreadsheets: The security gap your tools can’t see
When official systems can't support everyday workflows, employees turn to spreadsheets creating "shadow spreadsheets" that circulate unchecked. Grist shows how these spreadsheets expose sensitive data, create version sprawl, and remove the audit t
Published: 2025-12-12T10:01:11
New Windows RasMan zero-day flaw gets free, unofficial patches
Free unofficial patches are available for a new Windows zero-day vulnerability that allows attackers to crash the Remote Access Connection Manager (RasMan) service. [...]
Published: 2025-12-12T06:28:06
CISA orders feds to patch actively exploited Geoserver flaw
CISA has ordered U.S. federal agencies to patch a critical GeoServer vulnerability now actively exploited in XML External Entity (XXE) injection attacks. [...]
Published: 2025-12-12T04:48:31
Multiple Threat Actors Exploit React2Shell (CVE-2025-55182)
Written by: Aragorn Tseng, Robert Weiner, Casey Charrier, Zander Work, Genevieve Stark, Austin Larsen Introduction On Dec. 3, 2025, a critical unauthenticated remote code execution (RCE) vulnerability in React Server Components, tracked as CVE-2025
Published: 2025-12-12T14:00:00
Sanctioned but Still Spying: Intellexa’s Prolific Zero-Day Exploits Continue
Introduction Despite extensive scrutiny and public reporting, commercial surveillance vendors continue to operate unimpeded. A prominent name continues to surface in the world of mercenary spyware, Intellexa. Known for its “Predator” spyware, the c
Published: 2025-12-03T14:00:00
Wave of Tax Cuts Has Left Many States Vulnerable to Trump SNAP and Medicaid Crisis
The post Wave of Tax Cuts Has Left Many States Vulnerable to Trump SNAP and Medicaid Crisis appeared first on ProPublica. This fall, Americans got to see what it’s like to go without a safety net for the hungry. With the U.S. government shut down f
Published: 2025-12-09T10:00:00
Microsoft Patch Tuesday, December 2025 Edition
Microsoft today pushed updates to fix at least 56 security flaws in its Windows operating systems and supported software. This final Patch Tuesday of 2025 tackles one zero-day bug that is already being exploited, as well as two publicly disclosed vul... 
Published: 2025-12-09T23:18:29
SMS Phishers Pivot to Points, Taxes, Fake Retailers
China-based phishing groups blamed for non-stop scam SMS messages about a supposed wayward package or unpaid toll fee are promoting a new offering, just in time for the holiday shopping season: Phishing kits for mass-creating fake but convincing e-co... 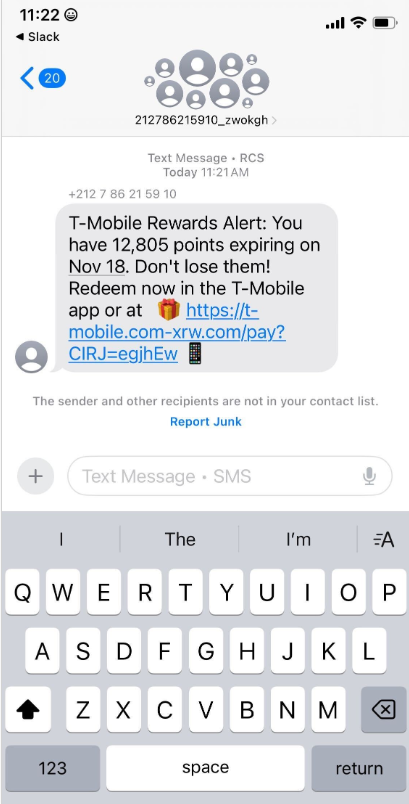
Published: 2025-12-04T23:02:34
‘Cyberpunk 2077’ Proved a Game Can Change Itself, But Not Its History
It ain't a thing of beauty, but 'Cyberpunk 2077' eventually became a good game that knows how it got there. It ain't a thing of beauty, but 'Cyberpunk 2077' eventually became a good game that knows how it got there.
Published: 2025-12-13T17:25:31
Honeypots can help defenders, or damn them if implemented badly
PLUS: Crims could burn your AI budgets thanks to weak defaults; CISA's top 25 vulns for 2025; And more Infosec In Brief The UK's National Cyber Security Centre (NCSC) has found that cyber-deception tactics such as honeypots and decoy accounts designed to fool attackers can be useful if implemented very carefully.
Published: 2025-12-14T23:26:27
Microsoft RasMan DoS 0-day gets unofficial patch - and a working exploit
Exploit hasn't been picked up by any malware detection engines, CEO tells The Reg A Microsoft zero-day vulnerability that allows an unprivileged user to crash the Windows Remote Access Connection Manager (RasMan) service now has a free, unofficial patch - with no word as to when Redmond plans to release an official one - along with a working exploit circulating online.
Published: 2025-12-12T22:29:33
New React vulns leak secrets, invite DoS attacks
And the earlier React2Shell patch is vulnerable If you're running React Server Components, you just can't catch a break. In addition to already-reported flaws, newly discovered bugs allow attackers to hang vulnerable servers and potentially leak Server Function source code, so anyone using RSC or frameworks that support it should patch quickly.
Published: 2025-12-12T18:23:30
Microsoft promises more bug payouts, with or without a bounty program
Critical vulnerabilities found in third-party applications eligible for award under 'in scope by default' move Microsoft is overhauling its bug bounty program to reward exploit hunters for finding vulnerabilities across all its products and services, even those without established bounty schemes.
Published: 2025-12-12T13:35:12
Uncle Sam sues ex-Accenture manager over Army cloud security claims
Justice Department alleges federal auditors were misled over compliance with FedRAMP and DoD requirements The US is suing a former senior manager at Accenture for allegedly misleading the government about the security of an Army cloud platform.
Published: 2025-12-12T13:25:09
UK watchdog urged to probe GDPR failures in Home Office eVisa rollout
Rights groups say digital-only record is leaking data and courting trouble Civil society groups are urging the UK's data watchdog to investigate whether the Home Office's digital-only eVisa scheme is breaching GDPR, sounding the alarm about systemic data errors and design failures that are exposing sensitive personal information while leaving migrants unable to prove their lawful status.
Published: 2025-12-12T12:36:34
Half of exposed React servers remain unpatched amid active exploitation
Wiz says React2Shell attacks accelerating, ranging from cryptominers to state-linked crews Half of the internet-facing systems vulnerable to a fast-moving React remote code execution flaw remain unpatched, even as exploitation has exploded into more than a dozen active attack clusters ranging from bargain-basement cryptominers to state-linked intrusion tooling.
Published: 2025-12-12T11:31:09
Crypto-crasher Do Kwon jailed for 15 years over $40bn UST bust
Judge said his fraud was on 'epic, generational scale' Terraform Labs founder Do Kwon will spend 15 years in jail after pleading guilty to committing fraud.
Published: 2025-12-12T01:53:15
Russian hackers debut simple ransomware service, but store keys in plain text
Operators accidentally left a way for you to get your data back CyberVolk, a pro-Russian hacktivist crew, is back after months of silence with a new ransomware service. There's some bad news and some good news here.
Published: 2025-12-11T20:56:37
Google fixes super-secret 8th Chrome 0-day
No details, no CVE, update your browser now Google issued an emergency fix for a Chrome vulnerability already under exploitation, which marks the world's most popular browser's eighth zero-day bug of 2025.
Published: 2025-12-11T17:09:31
LastPass hammered with 1.2M fine for 2022 breach fiasco
UK data regulator says failures were unacceptable for a company managing the world's passwords The UK's Information Commissioner's Office (ICO) says LastPass must cough up 1.2 million ($1.6 million) after its two-part 2022 data breach compromised information from up to 1.6 million UK users.
Published: 2025-12-11T16:45:55
Researcher claims Salt Typhoon spies attended Cisco training scheme
Skills gained later fed Beijing's cyber operations, according to SentinelLabs expert A security researcher specializing in tracking China threats claims two of Salt Typhoon's members were former attendees of a training scheme run by Cisco.
Published: 2025-12-11T12:42:26
10K Docker images spray live cloud creds across the internet
Flare warns devs are unwittingly publishing production-level secrets Docker Hub has quietly become a treasure trove of live cloud keys and credentials, with more than 10,000 public container images exposing sensitive secrets from over 100 companies, including a Fortune 500 firm and a major bank.
Published: 2025-12-11T11:26:29
Users report chaos as Legal Aid Agency stumbles back online after cyberattack
Workers frustrated with security-first changes to workflows and teething issues Exclusive Seven months after a landmark cyberattack, the UK's Legal Aid Agency (LAA) says it's returning to pre-breach operations, although law firms are still wrestling with buggy and more laborious systems.
Published: 2025-12-11T09:30:06
700+ self-hosted Gits battered in 0-day attacks with no fix imminent
More than half of internet-exposed instances already compromised Attackers are actively exploiting a zero-day bug in Gogs, a popular self-hosted Git service, and the open source project doesn't yet have a fix.
Published: 2025-12-10T21:31:45
US extradites Ukrainian woman accused of hacking meat processing plant for Russia
The digital intrusion allegedly caused thousands of pounds of meat to spoil and triggered an ammonia leak in the facility A Ukrainian woman accused of hacking US public drinking water systems and a meat processing facility on behalf of Kremlin-backed cyber groups was extradited to the US earlier this year and will stand trial in early 2026.
Published: 2025-12-10T17:56:59
Microsoft won't fix .NET RCE bug affecting slew of enterprise apps, researchers say
Devs and users should know better, Microsoft tells watchTowr Updated Security researchers have revealed a .NET security flaw thought to affect a host of enterprise-grade products that they say Microsoft refuses to fix.
Published: 2025-12-10T17:30:39
Protecting value at risk - the role of a risk operations center
Why should Keith Richards fingers inform your approach to risk? Partner Content For years, celebrities have insured their body parts for vast sums of money. Mariah Carey allegedly insured her voice and legs for $70 million during a tour, according to TMZ; and Lloyd's of London was reported to have insured a wide range of celebrity body parts, from restauranteur Egon Ronay's taste buds to the fingers of Rolling Stones guitarist Keith Richards, which were insured for $1.6 million.
Published: 2025-12-10T16:00:14
Crisis in Icebergen: How NATO crafts stories to sharpen cyber skills
1,500 military digital defenders spent the past week cleaning up a series of cyberattacks on fictional island feature Andravia and Harbadus two nations so often at odds with one another were once again embroiled in conflict over the past seven days, which thoroughly tested NATO's cybersecurity experts' ability to coordinate defenses across battlefield domains.
Published: 2025-12-10T12:29:07
Microsoft reports 7.8-rated zero day, plus 56 more in December Patch Tuesday
Plus critical critical Notepad++, Ivanti, and Fortinet updates, and one of these patches an under-attack security hole Updated Happy December Patch Tuesday to all who celebrate. This month's patch party includes one Microsoft flaw under exploitation, plus two others listed as publicly known but just 57 CVEs in total from Redmond.
Published: 2025-12-09T23:42:11
How to answer the door when the AI agents come knocking
Identity management vendors like Okta see an opening to calm CISOs worried about agents running amok The fear of AI agents running amok has thus far halted the wide deployment of these digital workhorses, Okta's president of Auth0, Shiv Ramji, told The Register.
Published: 2025-12-09T21:46:07
Porsche panic in Russia as pricey status symbols forget how to car
Satellite silence trips immobilizers, leaving owners stuck Hundreds of Porsches in Russia were rendered immobile last week, raising speculation of a hack, but the German carmaker tells The Register that its vehicles are secure.
Published: 2025-12-09T17:16:59
As humanoid robots enter the mainstream, security pros flag the risk of botnets on legs
Have we learned nothing from sci-fi films and TV shows? Interview Imagine botnets in physical form and you've got a pretty good idea of what could go wrong with the influx of AI-infused humanoid robots expected to integrate into society over the next few decades.
Published: 2025-12-09T15:00:10
UK to Europe: The time to counter Russia's information war machine is now
Foreign secretary set to address senior diplomats later today The UK's foreign secretary is calling for closer collaboration with Europe to combat the growing threat of information warfare as hybrid attacks target countries on the continent.
Published: 2025-12-09T12:49:33
UK finally vows to look at 35-year-old Computer Misuse Act
As Portugal gives researchers a pass under cybersecurity law Portugal has become the latest country to carve out protections for researchers under its cybersecurity law.
Published: 2025-12-09T10:15:13
Whitehall rejects 1.8B digital ID price tag but won't say what it will cost
Officials insist OBR relied on 'early estimate' and real figure won't emerge until next year The head of the department delivering the UK government's digital identity scheme has rejected the 1.8 billion cost forecast by the Office for Budget Responsibility (OBR), but is not willing to provide an alternative until after a delayed consultation on the plans.
Published: 2025-12-09T09:30:09
Researchers spot 700 percent increase in hypervisor ransomware attacks
Get your Hyper-V and VMware ESXi setups in order, people Researchers at security software vendor Huntress say they ve noticed a huge increase in ransomware attacks on hypervisors and urged users to ensure they re as secure as can be and properly backed up.
Published: 2025-12-09T06:41:27
193 cybercrims arrested, accused of plotting 'violence-as-a-service'
Minors groomed to kill and intimidate victims Nearly 200 people, including minors accused of involvement in murder plots, have been arrested over the last six months as part of Europol's Operational Taskforce (OTF) GRIMM. The operation targets what cops call "violence-as-a-service" - crime crews recruiting kids and teens online to carry out contract killings and other real-world attacks.
Published: 2025-12-08T18:45:28
UK moves to strengthen undersea cable defenses as Russian snooping ramps up
Atlantic Bastion combines AI systems with warships to counter increased surveillance The UK government has announced enhanced protection for undersea cables using autonomous vessels alongside crewed warships and aircraft, responding to escalating Russian surveillance activities.
Published: 2025-12-08T14:00:15
Home Office kept police facial recognition flaws to itself, UK data watchdog fumes
Regulator disappointed as soon-to-be-scrapped algo's problems remained a secret despite consistent engagement The UK's data protection watchdog has criticized the Home Office for failing to disclose significant biases in police facial recognition technology, despite regular engagement between the organizations.
Published: 2025-12-08T12:16:12
Barts Health seeks High Court block after Clop pillages NHS trust data
Body confirms patient and staff details siphoned via Oracle EBS flaw as gang threatens to leak haul Barts Health NHS Trust has confirmed that patient and staff data was stolen in Clop's mass-exploitation of Oracle's E-Business Suite (EBS), and says it is now taking legal action in an effort to stop the gang publishing any of the snatched information.
Published: 2025-12-08T11:12:05
Block all AI browsers for the foreseeable future: Gartner
Analysts worry lazy users could have agents complete mandatory infosec training, and attackers could do far nastier things Agentic browsers are too risky for most organizations to use, according to analyst firm Gartner.
Published: 2025-12-08T04:57:17
China's first reusable rocket explodes, but its onboard Ethernet network flew
PLUS: South Korea to strengthen security standards; Canon closes Chinese printer plant; APAC datacenter capacity to triple by 2029; And more Asia In Brief Chinese rocketry outfit LandSpace last week flew what it hoped would be the country's first reusable rocket, only to watch it explode while attempting to land.
Published: 2025-12-08T01:56:33
Apache warns of 10.0-rated flaw in Tika metadata ingestion tool
PLUS: New kind of DDOS from the Americas; Predator still hunting spyware targets; NIST issues IoT advice; And more! Infosec in Brief The Apache Foundation last week warned of a 10.0-rated flaw in its Tika toolkit.
Published: 2025-12-08T00:10:04
Death to one-time text codes: Passkeys are the new hotness in MFA
Wanna know a secret? Whether you're logging into your bank, health insurance, or even your email, most services today do not live by passwords alone. Now commonplace, multifactor authentication (MFA) requires users to enter a second or third proof of identity. However, not all forms of MFA are created equal, and the one-time passwords orgs send to your phone have holes so big you could drive a truck through them.
Published: 2025-12-06T09:11:12
Crims using social media images, videos in 'virtual kidnapping' scams
Proof of life? Or an active social media presence? Criminals are altering social media and other publicly available images of people to use as fake proof of life photos in "virtual kidnapping" and extortion scams, the FBI warned on Friday.
Published: 2025-12-05T23:23:39
Novel clickjacking attack relies on CSS and SVG
Who needs JavaScript? Security researcher Lyra Rebane has devised a novel clickjacking attack that relies on Scalable Vector Graphics (SVG) and Cascading Style Sheets (CSS).
Published: 2025-12-05T21:55:13
Cloudflare blames Friday outage on borked fix for React2shell vuln
Security community needs to rally and share more info faster, one researcher says Amid new reports of attackers pummeling a maximum security hole (CVE-2025-55182) in the React JavaScript library, Cloudflare's technology chief said his company took down its own network, forcing a widespread outage early Friday, to patch React2Shell.
Published: 2025-12-05T21:46:33
Asus supplier hit by ransomware attack as gang flaunts alleged 1 TB haul
Laptop maker says a vendor breach exposed some phone camera code, but not its own systems Asus has admitted that a third-party supplier was popped by cybercrims after the Everest ransomware gang claimed it had rifled through the tech titan's internal files.
Published: 2025-12-05T14:51:51
Beijing-linked hackers are hammering max-severity React bug, AWS warns
State-backed attackers started poking flaw as soon as it dropped anyone still unpatched is on borrowed time Amazon has warned that China-nexus hacking crews began hammering the critical React "React2Shell" vulnerability within hours of disclosure, turning a theoretical CVSS-10 hole into a live-fire incident almost immediately.
Published: 2025-12-05T14:10:12
UK pushes ahead with facial recognition expansion despite civil liberties backlash
Plan would create statutory powers for police use of biometrics, prompting warnings of mass surveillance The UK government has kicked off plans to ramp up police use of facial recognition, undeterred by a mounting civil liberties backlash and fresh warnings that any expansion risks turning public spaces into biometric dragnets.
Published: 2025-12-05T11:14:10
Bots, bias, and bunk: How can you tell what's real on the net?
You can improve the odds by combining skepticism, verification habits, and a few technical checks Opinion Liars, cranks, and con artists have always been with us. It's just that nowadays their reach has gone from the local pub to the globe.
Published: 2025-12-05T09:30:08
An AI for an AI: Anthropic says AI agents require AI defense
Automated software keeps getting better at pilfering cryptocurrency Anthropic could have scored an easy $4.6 million by using its Claude AI models to find and exploit vulnerabilities in blockchain smart contracts.
Published: 2025-12-05T00:30:02
PRC spies Brickstormed their way into critical US networks and remained hidden for years
'Dozens' of US orgs infected Chinese cyberspies maintained long-term access to critical networks sometimes for years and used this access to infect computers with malware and steal data, according to Thursday warnings from government agencies and private security firms.
Published: 2025-12-04T22:10:41
Hegseth needs to go to secure messaging school, report says
He's not alone: DoD inspector general says the whole Defense Department has a messaging security problem US Defense Secretary Pete Hegseth definitely broke the rules when he sent sensitive information to a Signal chat group, say Pentagon auditors, but he's not the only one using insecure messaging, and everyone needs better training.
Published: 2025-12-04T21:09:10
Twins who hacked State Dept hired to work for gov again, now charged with deleting databases
And then they asked an AI to help cover their tracks Vetting staff who handle sensitive government systems is wise, and so is cutting off their access the moment they're fired. Prosecutors say a federal contractor learned this the hard way when twin brothers previously convicted of hacking-related offenses allegedly used lingering access to delete nearly 100 government databases, including systems tied to Homeland Security and other agencies, within minutes of being terminated.
Published: 2025-12-04T19:48:14
Microsoft quietly shuts down Windows shortcut flaw after years of espionage abuse
Silent Patch Tuesday mitigation ends ability to hide malicious commands in .lnk files Microsoft has quietly closed off a critical Windows shortcut file bug long abused by espionage and cybercrime networks.
Published: 2025-12-04T15:01:04
Aisuru botnet turns Q3 into a terabit-scale stress test for the entire internet
Cloudflare data shows 29.7 Tbps record-breaker landed amid 87% surge in network-layer attacks The internet has spent the past three months ducking for cover as the Aisuru botnet hurled record-shattering DDoS barrages from an army of up to 4 million infected machines.
Published: 2025-12-04T13:07:02
TLS 1.3 includes welcome improvements, but still allows long-lived secrets
Tricky tradeoffs are hard to avoid when designing systems, but the choice not to use LLMs for some tasks is clear Systems Approach As we neared the finish line for our network security book, I received a piece of feedback from Brad Karp that my explanation of forward secrecy in the chapter on TLS (Transport Layer Security) was not quite right.
Published: 2025-12-04T04:30:07
Rust core library partly polished for industrial safety spec
Ferrous Systems achieves IEC 61508 (SIL 2) certification for systems that demand reliability Memory-safe Rust code can now be more broadly applied in devices that require electronic system safety, at least as measured by International Electrotechnical Commission (IEC) standards.
Published: 2025-12-04T01:11:12
AI Toys for Kids Talk About Sex, Drugs, and Chinese Propaganda
Plus: Travelers to the US may have to hand over five years of social media history, South Korean CEOs are resigning due to cyberattacks, and more.
Published: 2025-12-13T11:30:00
Warnings Mount in Congress Over Expanded US Wiretap Powers
Experts tell US lawmakers that a crucial spy program’s safeguards are failing, allowing intel agencies deeper, unconstrained access to Americans’ data.
Published: 2025-12-11T22:15:56
Doxers Posing as Cops Are Tricking Big Tech Firms Into Sharing People’s Private Data
A spoofed email address and an easily faked document is all it takes for major tech companies to hand over your most personal information.
Published: 2025-12-11T18:54:50
2 Men Linked to China’s Salt Typhoon Hacker Group Likely Trained in a Cisco ‘Academy’
The names of two partial owners of firms linked to the Salt Typhoon hacker group also appeared in records for a Cisco training program years before the group targeted Cisco’s devices in a spy campaign.
Published: 2025-12-10T17:00:00
A Complete Guide to the Jeffrey Epstein Document Dumps
New records about the infamous sex offender are released seemingly every week. Here’s a quick rundown of who’s releasing the Epstein documents, what they contain and what they’re releasing next.
Published: 2025-12-10T15:26:18
The US Won't Sanction China for Salt Typhoon Hacking
Plus: Officials warn of a disturbingly stealthy Chinese malware specimen, a CISA nomination stalls, and more.
Published: 2025-12-06T11:30:00
Huge Trove of Nude Images Leaked by AI Image Generator Startup’s Exposed Database
An AI image generator startup’s database was left accessible to the open internet, revealing more than 1 million images and videos, including photos of real people who had been “nudified.”
Published: 2025-12-05T11:00:00
‘Signalgate’ Inspector General Report Wants Just One Change to Avoid a Repeat Debacle
The United States Inspector General report reviewing Secretary of Defense Pete Hegseth’s text messaging mess recommends a single change to keep classified material secure.
Published: 2025-12-05T00:02:32
Cloudflare Has Blocked 416 Billion AI Bot Requests Since July 1
Cloudflare CEO Matthew Prince claims the internet infrastructure company’s efforts to block AI crawlers are already seeing big results.
Published: 2025-12-04T22:04:31
FBI Says DC Pipe Bomb Suspect Brian Cole Kept Buying Bomb Parts After January 6
The 30-year-old Virginia resident evaded capture for years after authorities discovered pipe bombs planted near buildings in Washington, DC, the day before the January 6, 2021, Capitol attack.
Published: 2025-12-04T19:42:18
A New Anonymous Phone Carrier Lets You Sign Up With Nothing but a Zip Code
Privacy stalwart Nicholas Merrill spent a decade fighting an FBI surveillance order. Now he wants to sell you phone service without knowing almost anything about you.
Published: 2025-12-04T17:00:00
The Louisiana Department of Wildlife and Fisheries Is Detaining People for ICE
Louisiana’s hunting and wildlife authority is one of more than 1,000 state and local agencies that have partnered with US immigration authorities this year alone.
Published: 2025-12-04T11:30:00
Russia Wants This Mega Missile to Intimidate the West, but It Keeps Crashing
One of Vladimir Putin’s favorite sabers to rattle seems to have lost its edge.
Published: 2025-12-03T00:00:00
Your Data Might Determine How Much You Pay for Eggs
A newly enacted New York law requires retailers to say whether your data influences the price of basic goods like a dozen eggs or toilet paper, but not how.
Published: 2025-12-02T19:10:21
Flock Uses Overseas Gig Workers to Build Its Surveillance AI
An accidental leak revealed that Flock, which has cameras in thousands of US communities, is using workers in the Philippines to review and classify footage.
Published: 2025-12-01T14:00:00
The WIRED Guide to Digital Opsec for Teens
Practicing good “operations security” is essential to staying safe online. Here's a complete guide for teenagers (and anyone else) who wants to button up their digital lives.
Published: 2025-11-29T12:00:00
CISA Adds Actively Exploited Sierra Wireless Router Flaw Enabling RCE Attacks
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday added a high-severity flaw impacting Sierra Wireless AirLink ALEOS routers to its Known Exploited Vulnerabilities (KEV) catalog, following reports of active exploitation in the wild. CVE-2018-4063 (CVSS score: 8.8/9.9) refers to an unrestricted file upload vulnerability that could be exploited to achieve remote code
Published: 2025-12-13T18:03:00
Apple Issues Security Updates After Two WebKit Flaws Found Exploited in the Wild
Apple on Friday released security updates for iOS, iPadOS, macOS, tvOS, watchOS, visionOS, and its Safari web browser to address two security flaws that it said have been exploited in the wild, one of which is the same flaw that was patched by Google in Chrome earlier this week. The vulnerabilities are listed below - CVE-2025-43529 (CVSS score: N/A) - A use-after-free vulnerability in WebKit
Published: 2025-12-13T11:02:00
Fake OSINT and GPT Utility GitHub Repos Spread PyStoreRAT Malware Payloads
Cybersecurity researchers are calling attention to a new campaign that's leveraging GitHub-hosted Python repositories to distribute a previously undocumented JavaScript-based Remote Access Trojan (RAT) dubbed PyStoreRAT. "These repositories, often themed as development utilities or OSINT tools, contain only a few lines of code responsible for silently downloading a remote HTA file and executing
Published: 2025-12-13T00:20:00
New Advanced Phishing Kits Use AI and MFA Bypass Tactics to Steal Credentials at Scale
Cybersecurity researchers have documented four new phishing kits named BlackForce, GhostFrame, InboxPrime AI, and Spiderman that are capable of facilitating credential theft at scale. BlackForce, first detected in August 2025, is designed to steal credentials and perform Man-in-the-Browser (MitB) attacks to capture one-time passwords (OTPs) and bypass multi-factor authentication (MFA). The kit
Published: 2025-12-12T19:34:00
Securing GenAI in the Browser: Policy, Isolation, and Data Controls That Actually Work
The browser has become the main interface to GenAI for most enterprises: from web-based LLMs and copilots, to GenAI powered extensions and agentic browsers like ChatGPT Atlas. Employees are leveraging the power of GenAI to draft emails, summarize documents, work on code, and analyze data, often by copying/pasting sensitive information directly into prompts or uploading files. Traditional
Published: 2025-12-12T15:48:00
New React RSC Vulnerabilities Enable DoS and Source Code Exposure
The React team has released fixes for two new types of flaws in React Server Components (RSC) that, if successfully exploited, could result in denial-of-service (DoS) or source code exposure. The team said the issues were found by the security community while attempting to exploit the patches released for CVE-2025-55182 (CVSS score: 10.0), a critical bug in RSC that has since been weaponized in
Published: 2025-12-12T14:25:00
React2Shell Exploitation Escalates into Large-Scale Global Attacks, Forcing Emergency Mitigation
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has urged federal agencies to patch the recent React2Shell vulnerability by December 12, 2025, amid reports of widespread exploitation. The critical vulnerability, tracked as CVE-2025-55182 (CVSS score: 10.0), affects the React Server Components (RSC) Flight protocol. The underlying cause of the issue is an unsafe deserialization
Published: 2025-12-12T14:11:00
CISA Flags Actively Exploited GeoServer XXE Flaw in Updated KEV Catalog
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a high-severity security flaw impacting OSGeo GeoServer to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation in the wild. The vulnerability in question is CVE-2025-58360 (CVSS score: 8.2), an unauthenticated XML External Entity (XXE) flaw that affects all versions prior to
Published: 2025-12-12T10:31:00
ThreatsDay Bulletin: Spyware Alerts, Mirai Strikes, Docker Leaks, ValleyRAT Rootkit and 20 More Stories
This week’s cyber stories show how fast the online world can turn risky. Hackers are sneaking malware into movie downloads, browser add-ons, and even software updates people trust. Tech giants and governments are racing to plug new holes while arguing over privacy and control. And researchers keep uncovering just how much of our digital life is still wide open. The new Threatsday Bulletin
Published: 2025-12-11T19:10:00
NANOREMOTE Malware Uses Google Drive API for Hidden Control on Windows Systems
Cybersecurity researchers have disclosed details of a new fully-featured Windows backdoor called NANOREMOTE that uses the Google Drive API for command-and-control (C2) purposes. According to a report from Elastic Security Labs, the malware shares code similarities with another implant codenamed FINALDRAFT (aka Squidoor) that employs Microsoft Graph API for C2. FINALDRAFT is attributed to a
Published: 2025-12-11T18:46:00
The Impact of Robotic Process Automation (RPA) on Identity and Access Management
As enterprises refine their strategies for handling Non-Human Identities (NHIs), Robotic Process Automation (RPA) has become a powerful tool for streamlining operations and enhancing security. However, since RPA bots have varying levels of access to sensitive information, enterprises must be prepared to mitigate a variety of challenges. In large organizations, bots are starting to outnumber
Published: 2025-12-11T17:00:00
WIRTE Leverages AshenLoader Sideloading to Install the AshTag Espionage Backdoor
An advanced persistent threat (APT) known as WIRTE has been attributed to attacks targeting government and diplomatic entities across the Middle East with a previously undocumented malware suite dubbed AshTag since 2020. Palo Alto Networks Unit 42 is tracking the activity cluster under the name Ashen Lepus. Artifacts uploaded to the VirusTotal platform show that the threat actor has trained its
Published: 2025-12-11T16:30:00
Unpatched Gogs Zero-Day Exploited Across 700+ Instances Amid Active Attacks
A high-severity unpatched security vulnerability in Gogs has come under active exploitation, with more than 700 compromised instances accessible over the internet, according to new findings from Wiz. The flaw, tracked as CVE-2025-8110 (CVSS score: 8.7), is a case of file overwrite in the file update API of the Go-based self-hosted Git service. A fix for the issue is said to be currently in the
Published: 2025-12-11T16:00:00
Chrome Targeted by Active In-the-Wild Exploit Tied to Undisclosed High-Severity Flaw
Google on Wednesday shipped security updates for its Chrome browser to address three security flaws, including one it said has come under active exploitation in the wild. The vulnerability, rated high in severity, is being tracked under the Chromium issue tracker ID "466192044." Unlike other disclosures, Google has opted to keep information about the CVE identifier, the affected component, and
Published: 2025-12-11T12:39:00
Active Attacks Exploit Gladinet's Hard-Coded Keys for Unauthorized Access and Code Execution
Huntress is warning of a new actively exploited vulnerability in Gladinet's CentreStack and Triofox products stemming from the use of hard-coded cryptographic keys that have affected nine organizations so far. "Threat actors can potentially abuse this as a way to access the web.config file, opening the door for deserialization and remote code execution," security researcher Bryan Masters said.
Published: 2025-12-11T11:26:00
React2Shell Exploitation Delivers Crypto Miners and New Malware Across Multiple Sectors
React2Shell continues to witness heavy exploitation, with threat actors leveraging the maximum-severity security flaw in React Server Components (RSC) to deliver cryptocurrency miners and an array of previously undocumented malware families, according to new findings from Huntress. This includes a Linux backdoor called PeerBlight, a reverse proxy tunnel named CowTunnel, and a Go-based
Published: 2025-12-11T01:49:00
.NET SOAPwn Flaw Opens Door for File Writes and Remote Code Execution via Rogue WSDL
New research has uncovered exploitation primitives in the .NET Framework that could be leveraged against enterprise-grade applications to achieve remote code execution. WatchTowr Labs, which has codenamed the "invalid cast vulnerability" SOAPwn, said the issue impacts Barracuda Service Center RMM, Ivanti Endpoint Manager (EPM), and Umbraco 8. But the number of affected vendors is likely to be
Published: 2025-12-11T00:51:00
Three PCIe Encryption Weaknesses Expose PCIe 5.0+ Systems to Faulty Data Handling
Three security vulnerabilities have been disclosed in the Peripheral Component Interconnect Express (PCIe) Integrity and Data Encryption (IDE) protocol specification that could expose a local attacker to serious risks. The flaws impact PCIe Base Specification Revision 5.0 and onwards in the protocol mechanism introduced by the IDE Engineering Change Notice (ECN), according to the PCI Special
Published: 2025-12-10T19:02:00
Warning: WinRAR Vulnerability CVE-2025-6218 Under Active Attack by Multiple Threat Groups
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added a security flaw impacting the WinRAR file archiver and compression utility to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. The vulnerability, tracked as CVE-2025-6218 (CVSS score: 7.8), is a path traversal bug that could enable code execution. However, for exploitation
Published: 2025-12-10T17:24:00
Webinar: How Attackers Exploit Cloud Misconfigurations Across AWS, AI Models, and Kubernetes
Cloud security is changing. Attackers are no longer just breaking down the door; they are finding unlocked windows in your configurations, your identities, and your code. Standard security tools often miss these threats because they look like normal activity. To stop them, you need to see exactly how these attacks happen in the real world. Next week, the Cortex Cloud team at Palo Alto Networks
Published: 2025-12-10T17:24:00
Microsoft Issues Security Fixes for 56 Flaws, Including Active Exploit and Two Zero-Days
Microsoft closed out 2025 with patches for 56 security flaws in various products across the Windows platform, including one vulnerability that has been actively exploited in the wild. Of the 56 flaws, three are rated Critical, and 53 are rated Important in severity. Two other defects are listed as publicly known at the time of the release. These include 29 privilege escalation, 18 remote code
Published: 2025-12-10T14:20:00
Fortinet, Ivanti, and SAP Issue Urgent Patches for Authentication and Code Execution Flaws
Fortinet, Ivanti, and SAP have moved to address critical security flaws in their products that, if successfully exploited, could result in an authentication bypass and code execution. The Fortinet vulnerabilities affect FortiOS, FortiWeb, FortiProxy, and FortiSwitchManager and relate to a case of improper verification of a cryptographic signature. They are tracked as CVE-2025-59718 and
Published: 2025-12-10T10:20:00
North Korea-linked Actors Exploit React2Shell to Deploy New EtherRAT Malware
Threat actors with ties to North Korea have likely become the latest to exploit the recently disclosed critical React2Shell security flaw in React Server Components (RSC) to deliver a previously undocumented remote access trojan dubbed EtherRAT. "EtherRAT leverages Ethereum smart contracts for command-and-control (C2) resolution, deploys five independent Linux persistence mechanisms, and
Published: 2025-12-09T23:55:00
Four Threat Clusters Using CastleLoader as GrayBravo Expands Its Malware Service Infrastructure
Four distinct threat activity clusters have been observed leveraging a malware loader known as CastleLoader, strengthening the previous assessment that the tool is offered to other threat actors under a malware-as-a-service (MaaS) model. The threat actor behind CastleLoader has been assigned the name GrayBravo by Recorded Future's Insikt Group, which was previously tracking it as TAG-150. The
Published: 2025-12-09T21:31:00
Storm-0249 Escalates Ransomware Attacks with ClickFix, Fileless PowerShell, and DLL Sideloading
The threat actor known as Storm-0249 is likely shifting from its role as an initial access broker to adopt a combination of more advanced tactics like domain spoofing, DLL side-loading, and fileless PowerShell execution to facilitate ransomware attacks. "These methods allow them to bypass defenses, infiltrate networks, maintain persistence, and operate undetected, raising serious concerns for
Published: 2025-12-09T19:07:00
How to Streamline Zero Trust Using the Shared Signals Framework
Zero Trust helps organizations shrink their attack surface and respond to threats faster, but many still struggle to implement it because their security tools don’t share signals reliably. 88% of organizations admit they’ve suffered significant challenges in trying to implement such approaches, according to Accenture. When products can’t communicate, real-time access decisions break down. The
Published: 2025-12-09T17:00:00
Google Adds Layered Defenses to Chrome to Block Indirect Prompt Injection Threats
Google on Monday announced a set of new security features in Chrome, following the company's addition of agentic artificial intelligence (AI) capabilities to the web browser. To that end, the tech giant said it has implemented layered defenses to make it harder for bad actors to exploit indirect prompt injections that arise as a result of exposure to untrusted web content and inflict harm. Chief
Published: 2025-12-09T16:44:00
STAC6565 Targets Canada in 80% of Attacks as Gold Blade Deploys QWCrypt Ransomware
Canadian organizations have emerged as the focus of a targeted cyber campaign orchestrated by a threat activity cluster known as STAC6565. Cybersecurity company Sophos said it investigated almost 40 intrusions linked to the threat actor between February 2024 and August 2025. The campaign is assessed with high confidence to share overlaps with a hacking group known as Gold Blade, which is also
Published: 2025-12-09T15:05:00
Researchers Find Malicious VS Code, Go, npm, and Rust Packages Stealing Developer Data
Cybersecurity researchers have discovered two new extensions on Microsoft Visual Studio Code (VS Code) Marketplace that are designed to infect developer machines with stealer malware. The VS Code extensions masquerade as a premium dark theme and an artificial intelligence (AI)-powered coding assistant, but, in actuality, harbor covert functionality to download additional payloads, take
Published: 2025-12-09T13:37:00
Experts Confirm JS#SMUGGLER Uses Compromised Sites to Deploy NetSupport RAT
Cybersecurity researchers are calling attention to a new campaign dubbed JS#SMUGGLER that has been observed leveraging compromised websites as a distribution vector for a remote access trojan named NetSupport RAT. The attack chain, analyzed by Securonix, involves three main moving parts: An obfuscated JavaScript loader injected into a website, an HTML Application (HTA) that runs encrypted
Published: 2025-12-08T23:07:00
Weekly Recap: USB Malware, React2Shell, WhatsApp Worms, AI IDE Bugs & More
It’s been a week of chaos in code and calm in headlines. A bug that broke the internet’s favorite framework, hackers chasing AI tools, fake apps stealing cash, and record-breaking cyberattacks all within days. If you blink, you’ll miss how fast the threat map is changing. New flaws are being found, published, and exploited in hours instead of weeks. AI-powered tools meant to help developers
Published: 2025-12-08T18:14:00
How Can Retailers Cyber-Prepare for the Most Vulnerable Time of the Year?
The holiday season compresses risk into a short, high-stakes window. Systems run hot, teams run lean, and attackers time automated campaigns to get maximum return. Multiple industry threat reports show that bot-driven fraud, credential stuffing and account takeover attempts intensify around peak shopping events, especially the weeks around Black Friday and Christmas. Why holiday peaks
Published: 2025-12-08T17:28:00
Android Malware FvncBot, SeedSnatcher, and ClayRat Gain Stronger Data Theft Features
Cybersecurity researchers have disclosed details of two new Android malware families dubbed FvncBot and SeedSnatcher, as another upgraded version of ClayRat has been spotted in the wild. The findings come from Intel 471, CYFIRMA, and Zimperium, respectively. FvncBot, which masquerades as a security app developed by mBank, targets mobile banking users in Poland. What's notable about the malware
Published: 2025-12-08T16:30:00
Sneeit WordPress RCE Exploited in the Wild While ICTBroadcast Bug Fuels Frost Botnet Attacks
A critical security flaw in the Sneeit Framework plugin for WordPress is being actively exploited in the wild, per data from Wordfence. The remote code execution vulnerability in question is CVE-2025-6389 (CVSS score: 9.8), which affects all versions of the plugin prior to and including 8.3. It has been patched in version 8.4, released on August 5, 2025. The plugin has more than 1,700 active
Published: 2025-12-08T14:45:00
MuddyWater Deploys UDPGangster Backdoor in Targeted Turkey-Israel-Azerbaijan Campaign
The Iranian hacking group known as MuddyWater has been observed leveraging a new backdoor dubbed UDPGangster that uses the User Datagram Protocol (UDP) for command-and-control (C2) purposes. The cyber espionage activity targeted users in Turkey, Israel, and Azerbaijan, according to a report from Fortinet FortiGuard Labs. "This malware enables remote control of compromised systems by allowing
Published: 2025-12-08T12:16:00
Researchers Uncover 30+ Flaws in AI Coding Tools Enabling Data Theft and RCE Attacks
Over 30 security vulnerabilities have been disclosed in various artificial intelligence (AI)-powered Integrated Development Environments (IDEs) that combine prompt injection primitives with legitimate features to achieve data exfiltration and remote code execution. The security shortcomings have been collectively named IDEsaster by security researcher Ari Marzouk (MaccariTA). They affect popular
Published: 2025-12-06T20:54:00
Critical React2Shell Flaw Added to CISA KEV After Confirmed Active Exploitation
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday formally added a critical security flaw impacting React Server Components (RSC) to its Known Exploited Vulnerabilities (KEV) catalog following reports of active exploitation in the wild. The vulnerability, CVE-2025-55182 (CVSS score: 10.0), relates to a case of remote code execution that could be triggered by an
Published: 2025-12-06T17:10:00
Zero-Click Agentic Browser Attack Can Delete Entire Google Drive Using Crafted Emails
A new agentic browser attack targeting Perplexity's Comet browser that's capable of turning a seemingly innocuous email into a destructive action that wipes a user's entire Google Drive contents, findings from Straiker STAR Labs show. The zero-click Google Drive Wiper technique hinges on connecting the browser to services like Gmail and Google Drive to automate routine tasks by granting them
Published: 2025-12-05T23:23:00
Critical XXE Bug CVE-2025-66516 (CVSS 10.0) Hits Apache Tika, Requires Urgent Patch
A critical security flaw has been disclosed in Apache Tika that could result in an XML external entity (XXE) injection attack. The vulnerability, tracked as CVE-2025-66516, is rated 10.0 on the CVSS scoring scale, indicating maximum severity. "Critical XXE in Apache Tika tika-core (1.13-3.2.1), tika-pdf-module (2.0.0-3.2.1) and tika-parsers (1.13-1.28.5) modules on all platforms allows an
Published: 2025-12-05T21:53:00
Chinese Hackers Have Started Exploiting the Newly Disclosed React2Shell Vulnerability
Two hacking groups with ties to China have been observed weaponizing the newly disclosed security flaw in React Server Components (RSC) within hours of it becoming public knowledge. The vulnerability in question is CVE-2025-55182 (CVSS score: 10.0), aka React2Shell, which allows unauthenticated remote code execution. It has been addressed in React versions 19.0.1, 19.1.2, and 19.2.1. According
Published: 2025-12-05T19:40:00
Intellexa Leaks Reveal Zero-Days and Ads-Based Vector for Predator Spyware Delivery
A human rights lawyer from Pakistan's Balochistan province received a suspicious link on WhatsApp from an unknown number, marking the first time a civil society member in the country was targeted by Intellexa's Predator spyware, Amnesty International said in a report. The link, the non-profit organization said, is a "Predator attack attempt based on the technical behaviour of the infection
Published: 2025-12-05T17:17:00
"Getting to Yes": An Anti-Sales Guide for MSPs
Most MSPs and MSSPs know how to deliver effective security. The challenge is helping prospects understand why it matters in business terms. Too often, sales conversations stall because prospects are overwhelmed, skeptical, or tired of fear-based messaging. That’s why we created ”Getting to Yes”: An Anti-Sales Guide for MSPs. This guide helps service providers transform resistance into trust and
Published: 2025-12-05T17:00:00
CISA Reports PRC Hackers Using BRICKSTORM for Long-Term Access in U.S. Systems
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday released details of a backdoor named BRICKSTORM that has been put to use by state-sponsored threat actors from the People's Republic of China (PRC) to maintain long-term persistence on compromised systems. "BRICKSTORM is a sophisticated backdoor for VMware vSphere and Windows environments," the agency said. "
Published: 2025-12-05T13:44:00
JPCERT Confirms Active Command Injection Attacks on Array AG Gateways
A command injection vulnerability in Array Networks AG Series secure access gateways has been exploited in the wild since August 2025, according to an alert issued by JPCERT/CC this week. The vulnerability, which does not have a CVE identifier, was addressed by the company on May 11, 2025. It's rooted in Array's DesktopDirect, a remote desktop access solution that allows users to securely access
Published: 2025-12-05T11:10:00
Silver Fox Uses Fake Microsoft Teams Installer to Spread ValleyRAT Malware in China
The threat actor known as Silver Fox has been spotted orchestrating a false flag operation to mimic a Russian threat group in attacks targeting organizations in China. The search engine optimization (SEO) poisoning campaign leverages Microsoft Teams lures to trick unsuspecting users into downloading a malicious setup file that leads to the deployment of ValleyRAT (Winos 4.0), a known malware
Published: 2025-12-04T22:55:00
ThreatsDay Bulletin: Wi-Fi Hack, npm Worm, DeFi Theft, Phishing Blasts and 15 More Stories
Think your Wi-Fi is safe? Your coding tools? Or even your favorite financial apps? This week proves again how hackers, companies, and governments are all locked in a nonstop race to outsmart each other. Here’s a quick rundown of the latest cyber stories that show how fast the game keeps changing. DeFi exploit drains funds Critical yETH Exploit Used to Steal $9M
Published: 2025-12-04T17:28:00
5 Threats That Reshaped Web Security This Year [2025]
As 2025 draws to a close, security professionals face a sobering realization: the traditional playbook for web security has become dangerously obsolete. AI-powered attacks, evolving injection techniques, and supply chain compromises affecting hundreds of thousands of websites forced a fundamental rethink of defensive strategies. Here are the five threats that reshaped web security this year, and
Published: 2025-12-04T17:00:00
GoldFactory Hits Southeast Asia with Modified Banking Apps Driving 11,000+ Infections
Cybercriminals associated with a financially motivated group known as GoldFactory have been observed staging a fresh round of attacks targeting mobile users in Indonesia, Thailand, and Vietnam by impersonating government services. The activity, observed since October 2024, involves distributing modified banking applications that act as a conduit for Android malware, Group-IB said in a technical
Published: 2025-12-04T14:57:00
Record 29.7 Tbps DDoS Attack Linked to AISURU Botnet with up to 4 Million Infected Hosts
Cloudflare on Wednesday said it detected and mitigated the largest ever distributed denial-of-service (DDoS) attack that measured at 29.7 terabits per second (Tbps). The activity, the web infrastructure and security company said, originated from a DDoS botnet-for-hire known as AISURU, which has been linked to a number of hyper-volumetric DDoS attacks over the past year. The attack lasted for 69
Published: 2025-12-04T12:22:00
Critical RSC Bugs in React and Next.js Allow Unauthenticated Remote Code Execution
A maximum-severity security flaw has been disclosed in React Server Components (RSC) that, if successfully exploited, could result in remote code execution. The vulnerability, tracked as CVE-2025-55182, carries a CVSS score of 10.0. The vulnerability has been codenamed React2shell. It allows "unauthenticated remote code execution by exploiting a flaw in how React decodes payloads sent to React
Published: 2025-12-03T23:49:00
SECURITY AFFAIRS MALWARE NEWSLETTER ROUND 75
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape Malware Newsletter UDPGangster Campaigns Target Multiple Countries Ransomware Trends in Bank Secrecy Act Data Between 2022 and 2024 Return of ClayRat: Expanded Features and Techniques SEEDSNATCHER : Dissecting an Android Malware Targeting Multiple Crypto Wallet Mnemonic […]
Published: 2025-12-14T14:22:16
Security Affairs newsletter Round 554 by Pierluigi Paganini INTERNATIONAL EDITION
A new round of the weekly Security Affairs newsletter has arrived! Every week, the best security articles from Security Affairs are free in your email box. Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press. Experts found an unsecured 16TB database containing 4.3B professional records Germany calls in Russian Ambassador over […]
Published: 2025-12-14T14:03:10
Experts found an unsecured 16TB database containing 4.3B professional records
An open 16TB database exposed 4.3B professional records. It was unsecured and only closed after researchers alerted the owner. A 16TB unsecured MongoDB database exposed about 4.3 billion professional records, mainly LinkedIn-style data, enabling large-scale AI-driven social-engineering attacks. The researcher Bob Diachenko and nexos.ai discovered the unsecured DB on November 23, 2025, and it was […]
Published: 2025-12-14T08:56:50
Germany calls in Russian Ambassador over air traffic control hack claims
Germany summoned Russia’s ambassador over alleged cyberattacks on air traffic control and a disinformation campaign ahead of national elections. Germany summoned Russia’s ambassador after accusing Moscow of cyber attacks against its air traffic control authority and running a disinformation campaign ahead of February’s election. The German government announced it has clear evidence linking an August […]
Published: 2025-12-13T18:14:19
U.S. CISA adds Google Chromium and Sierra Wireless AirLink ALEOS flaws to its Known Exploited Vulnerabilities catalog
U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds Google Chromium and Sierra Wireless AirLink ALEOS flaws to its Known Exploited Vulnerabilities catalog. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added [1, 2] Microsoft Windows and WinRAR flaws to its Known Exploited Vulnerabilities (KEV) catalog. Below are the flaws added to the catalog: CVE-2025-14174 is an […]
Published: 2025-12-13T10:48:52
Emergency fixes deployed by Google and Apple after targeted attacks
Google and Apple issued emergency updates to address zero-day flaws exploited in attacks targeting an unknown number of users. Apple and Google have both pushed out urgent security updates after uncovering a highly targeted attacks against an unknown number of users. The attacks abused zero day vulnerabilities in their software. The campaign appears to involve nation-state […]
Published: 2025-12-13T00:08:15
Notepad++ fixed updater bugs that allowed malicious update hijacking
Notepad++ addressed an updater vulnerability that allows attackers hijack update traffic due to weak file authentication. Notepad++ addressed a flaw in its updater that allowed attackers to hijack update traffic due to improper authentication of update files in earlier versions. The popular security researcher Kevin Beaumont first reported that several Notepad++ users faced security incidents. […]
Published: 2025-12-12T22:16:28
Elastic detects stealthy NANOREMOTE malware using Google Drive as C2
Elastic found a new Windows backdoor, NANOREMOTE, similar to FINALDRAFT/REF7707, using the Google Drive API for C2. Elastic Security Labs researchers uncovered NANOREMOTE, a new Windows backdoor that uses the Google Drive API for C2. Elastic says it shares code with the FINALDRAFT (Squidoor) implant, which uses Microsoft Graph API and is linked to threat […]
Published: 2025-12-12T11:11:36
U.S. CISA adds an OSGeo GeoServer flaw to its Known Exploited Vulnerabilities catalog
U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds an OSGeo GeoServer flaw to its Known Exploited Vulnerabilities catalog. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added an OSGeo GeoServer flaw, tracked as CVE-2025-58360 (CVSS Score of 8.2), to its Known Exploited Vulnerabilities (KEV) catalog. GeoServer is an open-source server that allows users to share and edit geospatial […]
Published: 2025-12-12T09:24:42
Critical Gogs zero-day under attack, 700 servers hacked
Hackers exploited an unpatched Gogs zero-day, allowing remote code execution and compromising around 700 Internet-facing servers. Gogs is a self-hosted Git service, similar to GitHub, GitLab, or Bitbucket, but designed to be lightweight and easy to deploy. It allows individuals or organizations to host their own Git repositories on their servers, offering features like version […]
Published: 2025-12-11T21:29:59